What Is Pegasus Spyware?
Pegasus spyware has been around since at least 2012 and it’s a very sophisticated piece of malware that can be used to steal personal information from you or even turn off your device remotely. It was first discovered in China and then spread across Europe and North America.
With iOS 14.8, Apple has released a critical update for your iPhone that looks to patch a flaw that the Pegasus spyware exploited.
It works like this: A remote attacker sends malicious code via SMS message to a targeted mobile number. Once inside the victim’s smartphone, the malware installs itself onto the device and then begins monitoring everything from incoming texts to outgoing calls. If you’re worried about being tracked by someone else, there are ways to protect yourself.
The spyware can be remotely installed on a person’s iPhone or iPad, granting the person or organization full access to the device and all it’s data — without the owner’s knowledge or having to take any action. That includes text messages, emails and even recording phone calls. Pegasus was originally designed, and is marketed by its creator the NSO Group, to monitor criminals and terrorists. RIGHT!!
The good news is that there are ways to detect if you have this type of software installed on your smartphone. Chances that your device is infected is low, so don’t start worrying just yet! Here I will show you how to check. I personally did it and my scan came out clean. Better be safe than sorry!
How to run the Pegasus Spyware scan on your iPhone or iPad
- I recommend installing the iMazing program on your computer. (https://imazing.com/download) Don’t worry about getting the paid version, although I personally use it to backup all my iOS devices. The free trial will be enough for this. With iMazing installed and running, connect your iPhone or iPad to the computer. You may have to enter the Lock Screen code on your device to approve the connection before proceeding (something to keep in mind if your iPhone or iPad isn’t showing up in iMazing).
- Next, scroll down through the action options on the right-hand side of iMazing until you locate Detect Spyware; click it.
- A new window will open, guiding you through the process. The tool works by creating a local backup of your device (so you’ll need to make sure you have enough storage space for the backup), and then analyzing that backup. It’s an automated task, so you don’t have to stick around to monitor it once you click start.
iMazing suggests leaving all of the default settings in place as you click through each screen. There are configuration options built into the tool for advanced users, but for most of us, the default configuration settings will get the job done. - After going through the basic configuration, you’ll need to accept a license for the tool and then click the Start Analysis button.
- Once the process starts, make sure you leave your iPhone or iPad connected until it’s finished. I ran the test on my iPhone 12 Pro Max and it took around 30 minutes to create the backup and another five minutes for it to be analyzed. After the backup was created, I did have to enter my account password to allow iMazing to begin analyzing the file. Because of that, I recommend starting the tool and checking on it after a while.
Once iMazing begins analyzing your device’s backup, it’ll show you its progress by displaying each individual app it’s checking, starting with iMessage. The app is using a database of known ” malicious email addresses, links, process names and file names. When iMazing finishes, you’ll see an alert with the results. In my case, my iPhone 12 Pro showed no signs of infection but had 10 warnings, which in my case was that it could not expand some shortened URL’s. No concern there.
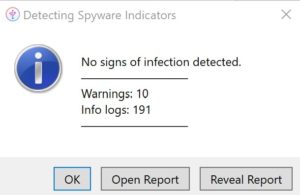
At the end of the scan, the results are displayed in an easy-to-read alert.
Note of warning: If you close the alert, I did not find a way to reopen it to look at the results of the scan. So Open Report (Will download an CSV file) or Reveal Report.
